Essential Eight Automated Auditing
The first fully automated security auditing solution designed to ensure organizational compliance with the ACSC’s Essential Eight cybersecurity framework.
SecurE8 operates autonomously, leveraging agentless technology to capture results across potentially thousands of endpoints without any dependencies or prerequisites.
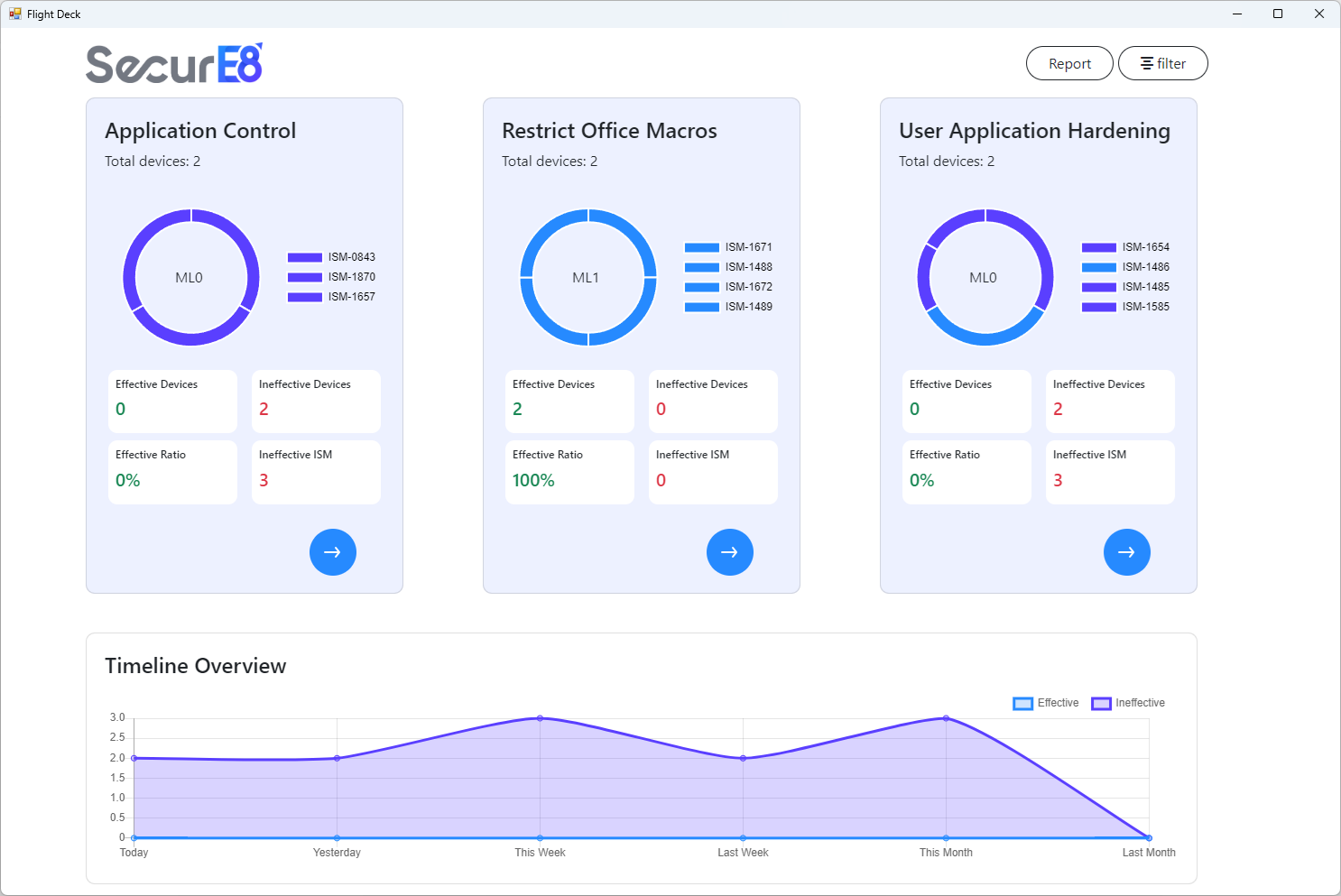
Additionally, its intuitive Flight Deck feature presents these findings in a streamlined, web-based interface.
The outcome is a comprehensive, innovative and automated approach to strengthened Essential Eight cyber defence.
Features 1

Real-Time Assurance
Continuous testing and monitoring of your Essential Eight security posture ensures a proactive and adaptive defense against evolving threats, keeping your organization secure and compliant in a dynamic cybersecurity landscape.
CISO Reporting
Dashboards on the Essential Eight Maturity Model provides an efficient, high-level view of your organisation's security posture. Meanwhile, detailed reporting with embedded artifacts streamlines audits, enhances accuracy, and simplifies compliance.
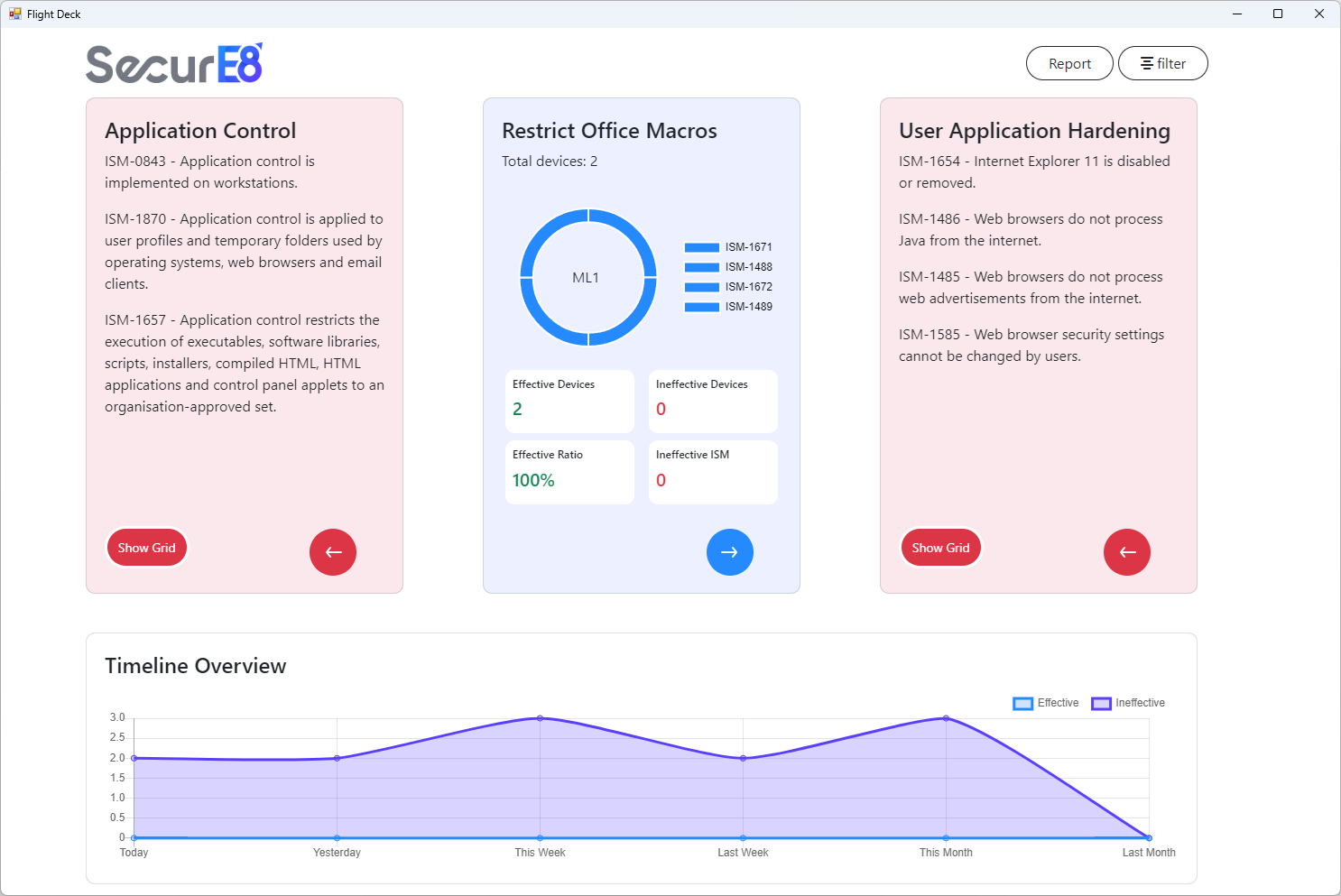
Holistic Viewpoint of Compliance
A high-level review of your organization’s Essential Eight Maturity gives a clear view of security effectiveness, shows progress over time, and supports decision-making to maintain and improve cybersecurity resilience.
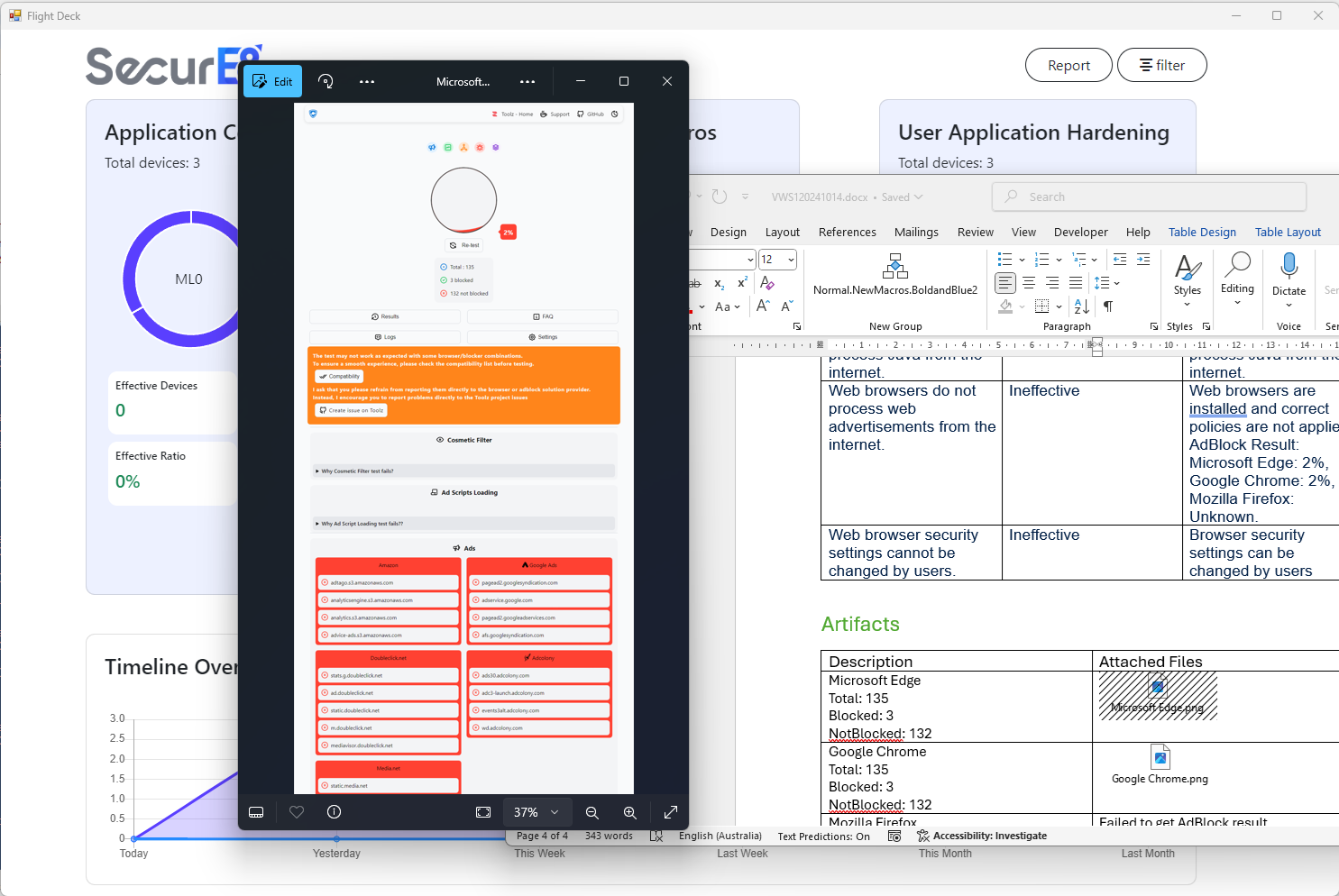
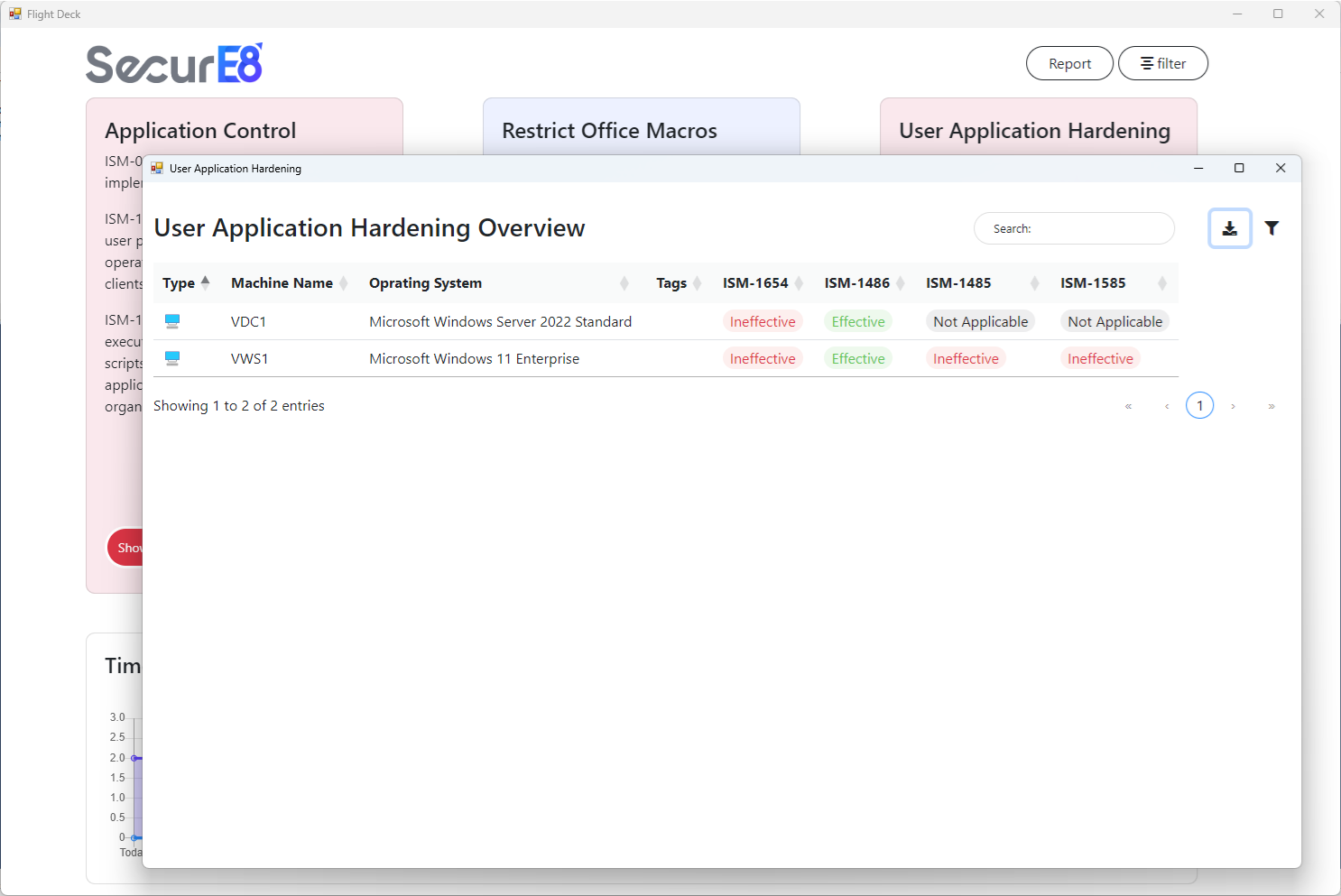
Device Specific Detail
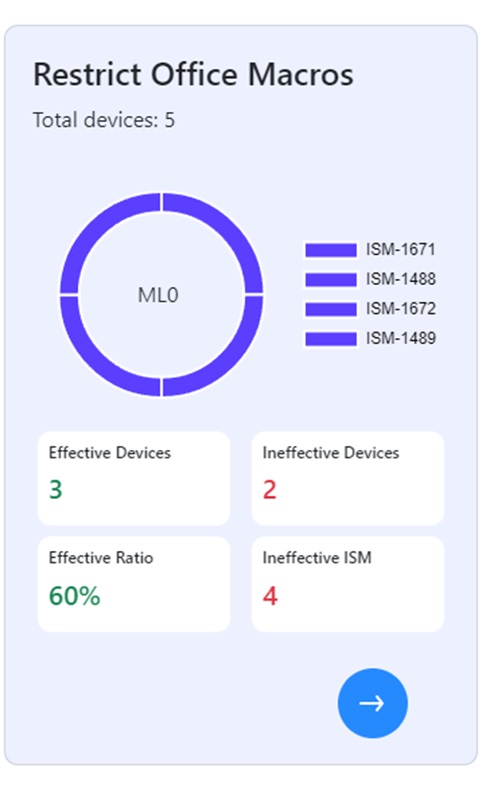
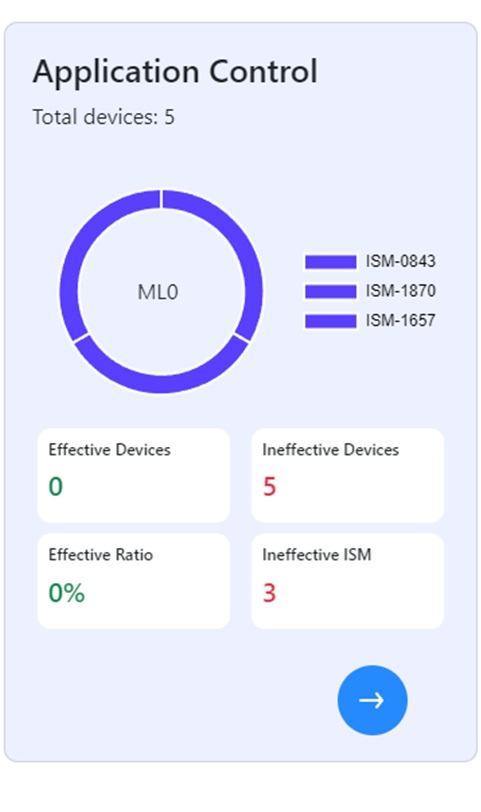
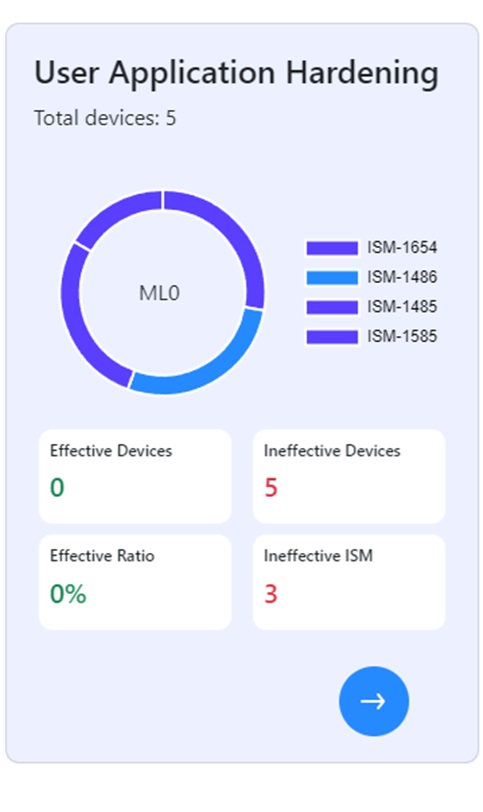
Granular device-level compliance information provides detailed visibility into the security posture of each machine, enabling auditors to investigate ISM control effectiveness, quickly identify issues, and ensure compliance through targeted corrective actions and efficient search capabilities.
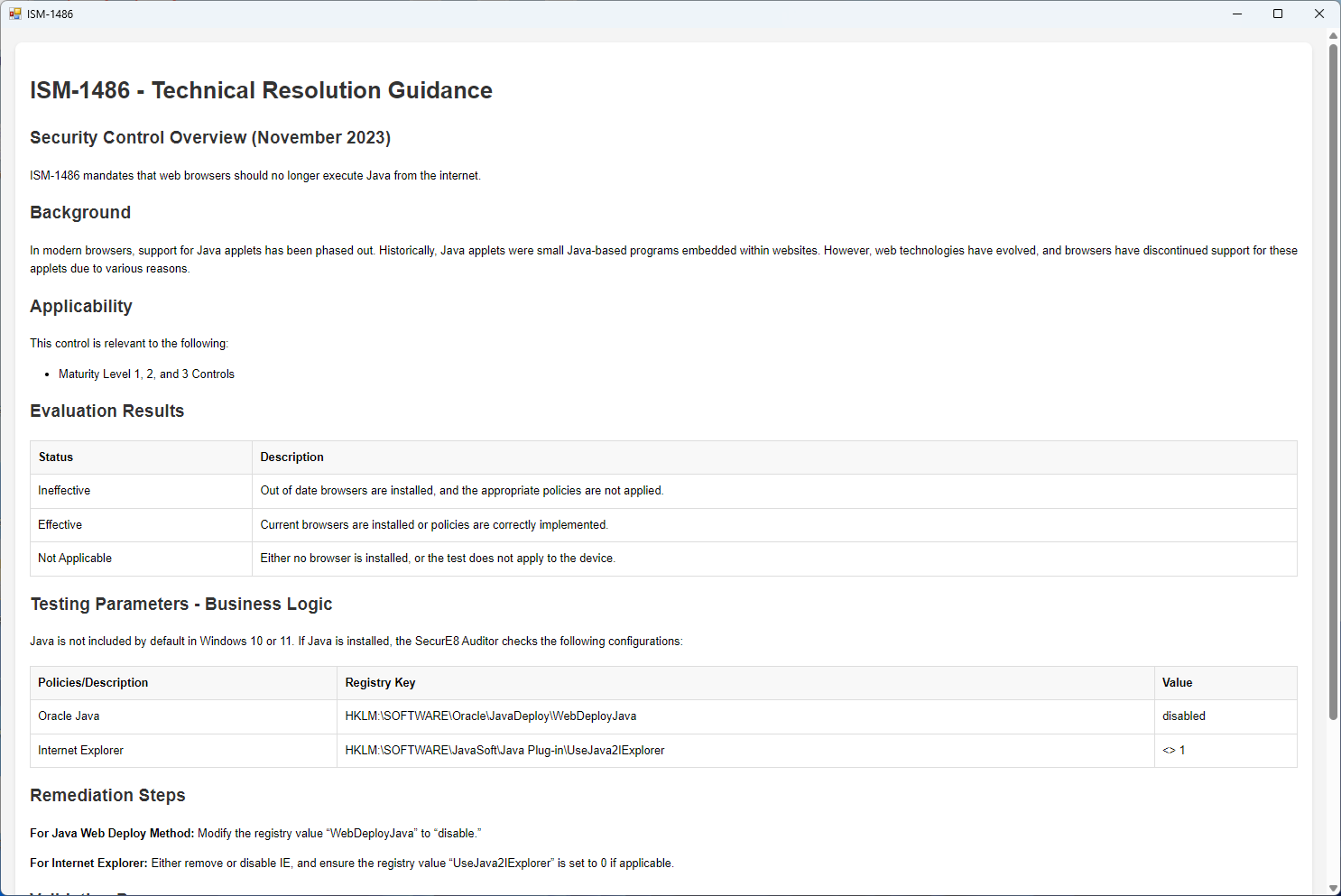
Remediation Advice
Operational and security uplifts are simplified by providing clear, actionable guidance to remediate Essential Eight compliance gaps, enabling even non-experts to perform audits effectively while streamlining communication and documentation for smoother implementation of security controls. No further need for the Essential Eight compliance guide.
Fanatical Support
We’re committed to providing exceptional governance risk and compliance software, answering your questions promptly and addressing your needs to a high standard. Feel free to get in touch with our essential 8 framework experts today.
Single pane of glass
Executive and CISO-ready dashboards and reports, presented on a single pane of glass, provide an efficient way to visualise your organization’s security posture. Tailored for executives, they offer a high-level overview to quickly understand your security status and make strategic decisions. This single interface consolidates all relevant data, eliminating the need for multiple sources.
Our platform also offers detailed reports with embedded artifacts like logs and screenshots, providing concrete evidence for audits. These reports will simplify the Protective Security Policy Framework (PSPF) compliance, generating comprehensive audit reports in seconds, saving time, and enhancing accuracy. Organizations can ensure their security practices are transparent and easily communicated to stakeholders.
Capture the Essential Eight audit data by running the auditor.
Display the captured data in the Flight Deck and build reports.
Why Choose SecurE8?
What are the key benifits?
- Automation and Efficiency: SecurE8 Auditor automates the complex processes required to meet the Essential 8 Maturity Model and Essential Eight Compliance, significantly reducing manual intervention and increasing data accuracy and efficiency. This automation drives substantial cost savings, enabling employees to focus on strategic initiatives that add long-term value to the organisation. With comprehensive support for the Essential 8 Framework, SecurE8 Auditor elevates operational standards, ensuring streamlined cyber security reporting aligned with best practices in compliance and risk management.
- Cybersecurity and Compliance: With its robust governance, risk, and compliance software capabilities, SecurE8 Auditor provides critical protections that align with the Essential Eight Cyber Security Controls, safeguarding sensitive data while ensuring regulatory compliance. This dual emphasis on cybersecurity and Essential 8 Security Maturity Model compliance makes SecurE8 Auditor a trusted solution for organisations looking to meet Protective Security Policy Framework (PSPF) standards and strengthen defences. It addresses the question of “what is compliance in cybersecurity?” by embedding both security and compliance into every process.
- Scalability and Integration: SecurE8 Auditor is built to scale alongside business growth and can integrate with other Essential 8 Maturity Model frameworks and risk management software, providing a cohesive solution for governance, risk, and compliance (GRC). This scalability ensures the platform remains aligned with evolving organisational needs, offering a unified view of compliance and risk management as requirements change.
Why is this important?
As stated on the Cyber.gov.au website: The Australian Signals Directorate (ASD) has developed a set of prioritised mitigation strategies, called the Essential Eight (E8), to help organisations protect their internet-connected IT networks from various cyber threats. This framework defines three maturity levels (from Maturity Level One to Three) that correspond to the increasing complexity of adversaries’ tools, tactics, techniques, and procedures. Additionally, a Maturity Level Zero is included to represent situations where the requirements of Maturity Level One are not yet met.
Get it nowWhen can I get uplifted?
We only produce and support the SecurE8 software and do not perform Essential Eight uplifts, however Tesserent Cyber Solutions are exceptional at this and they maintain a strong working relationship with the ACSC and have conducted numerous uplifts and audits for ACSC. Get in contact with them here.
Who developed this software?
Mission Statement
To empower government agencies with precise, efficient, and secure audit solutions that ensure continual compliance with critical cybersecurity frameworks, fostering resilience and trust in the digital landscape.
Overview
SecurE8 is Australian built software, founded by Canberra local company Bit Traders. The software was established with the mission to simplify and enhance the continuous auditing process for the Federal Government’s Protective Security Policy Framework (PSPF), with a particular emphasis on the Essential Eight—a vital set of mitigation strategies designed to strengthen government cybersecurity. By leveraging innovative technology and streamlined processes, SecurE8 aims to provide government agencies with an efficient, reliable, and cost-effective solution for meeting compliance standards. SecurE8’s focus on automation not only reduces manual effort but also improves audit accuracy, enabling agencies to proactively manage security risks while maintaining adherence to government requirements.
Which license is for me?
The software is paid commercial software, and there is no free or trial version. For organisations requiring full network audits, there is an ongoing annual licensing cost to maintain access and functionality. If you wish to perform a quick and effortless Essential Eight audit on a single device, you can purchase the single 30 day version.
These costs ensure that the software remains updated and capable of delivering high-quality audits that meet the evolving needs of businesses. For specific pricing details, you can refer to the shop page, where the current cost structure is outlined.
Upon download, the software is fully operational with unrestricted access to all features. However, it is the licensee’s responsibility to ensure the software is used within the scope of the license and protected from unauthorized distribution.